Since I have written a research paper on Net Neutrality I have decided to attach it below so that you can read it if you would like and see that I have spent time discussing the idea: Essay 2. Other than that I will attach a synopsis of my opinions on the issue below so that it is not necessary to read the essay.
How data is manipulated and presented is a prominent concern, especially regarding the current power dynamic between ISPs, the U.S. government and the users of the Internet. As technology advances, regulation and information segregation becomes easier and more commonplace. The router allows operators to prioritize or de-prioritize certain packets of data or even drop or remove them from their network altogether. This technology continues to evolve and allow operators to choose how to handle data packets for commercial or policy reasons as opposed to the network performance reasons. Packets can be favored because they originate from a preferred source or de-prioritized or even blocked simply because they originate from a non-preferred source. This prioritization or de-prioritization of data packets is often dubbed “access tiering” and it is at the core of the Net Neutrality debate.[1] The ability to handle data on different network tiers has ignited a high-profile debate in the United States about whether or not operators should be allowed to discriminate between data packets and, therefore, whether regulatory intervention is needed to constrain how operators run their networks.[2] Without regulation this opens the door for ISPs to differentiate the data pathways, allowing only some information through at their own discretion. That means an ISP could charge more to stream Netflix versus YouTube, or increase or slow a users browser speed based on price or data plan. This could create a complicated network of business alliances, restrictions on information and socioeconomic disparities. After pushback from the American people, the FCC reconstructed the Open Internet rules and adopted new rules on February 26th, 2015. These rules were designed to protect free expression and innovation on the Internet and promote investment in the nation’s broadband networks. The new rules apply to both fixed and mobile broadband services, recognizing advances in technology and the growing significance of mobile broadband Internet access in recent years. These rules restrict blocking so broadband providers may not block access to legal content, applications and services. It also restricts throttling; broadband providers may not impair or degrade lawful Internet traffic on the basis of content, applications, or services. Further, it restricts paid prioritization or “fast lanes”; broadband providers may not favor some lawful Internet traffic over other lawful traffic in exchange for consideration of any kind.[3] Even though actions have been taken, the concept of Net Neutrality and its place in our society is not resolved.
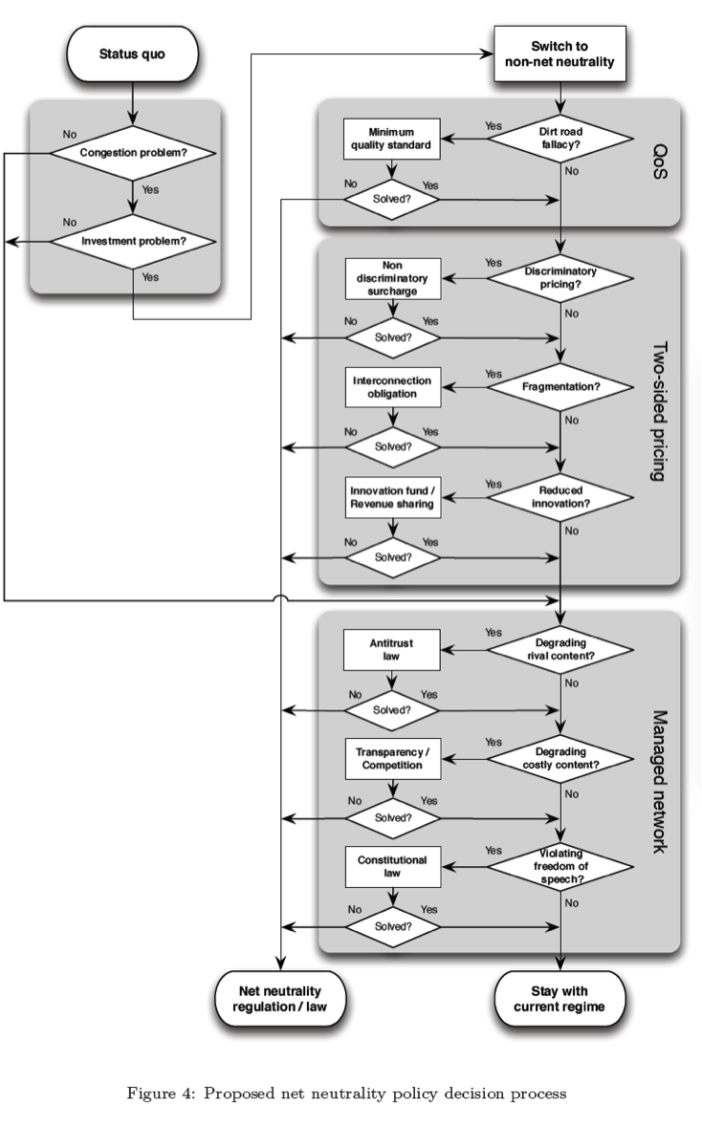
Moving forward with policy, it is important to understand that there must be some regulation of the Internet, and that there is already regulation on the Internet, as it exists today. The question is not whether to regulate cyberspace, but how to do so—within which forum, focusing on which layer, involving which actors, and according to which of many competing values. The regulation of cyberspace tends to take place behind the scenes, based on decisions taken by private actors rather than as a result of public deliberation, without even the knowledge of the public. As the trend toward the securitization and privatization of cyberspace continues, these problems are likely to become more, rather than less, acute.[4] The Net Neutrality rules that are put in place by the FCC are important and must be maintained and improved as the topography of the Internet continues to change. Open access to all content through an open channel is important regardless of medium or type of content. If the engineering behind the physical layer of the Internet changes and tiering must occur, it must be consumer-led, rather than operator-determined, access tiering. It must be matched with meaningful disclosure requirements and contractual protections best balance the reasonable demand that there be an incentive to invest in Internet infrastructure with the public interest in a ‘non-discriminatory’ Internet.”[5] A Net Neutrality policy decision map (See Appendix 2) is important to help understand the steps that must be taken and the process that must follow in order to further address the Net Neutrality debate. The U.S. debate on Net Neutrality has generally been centered on what ISPs could or could not do unless the laws are put into place, which is what they are currently doing at the moment. In this way, it will require a steady raising of awareness, the channeling of ingenuity into productive avenues, and the implementation of liberal-democratic restraints.[6] Even though it is a slow process, actions and legislation must be pushed forward to prevent the upheaval of the Internet instead of waiting for it to be irrevocably changed.
References:
[1] Ganley, Paul and Ben Allgrove. “Net Neutrality: A Users Guide.” 454.
[2] Ganley, Paul and Ben Allgrove. “Net Neutrality: A Users Guide.” 455.
[3] Open Internet. Federal Communcations Commission. May 2, 2015. FCC.gov.
[4] Nissenbaum, Helen. Privacy in Context. 56.
[5] Ganley, Paul and Ben Allgrove. “Net Neutrality: A Users Guide.” 463.
[6] Nissenbaum, Helen. Privacy in Context. 56.